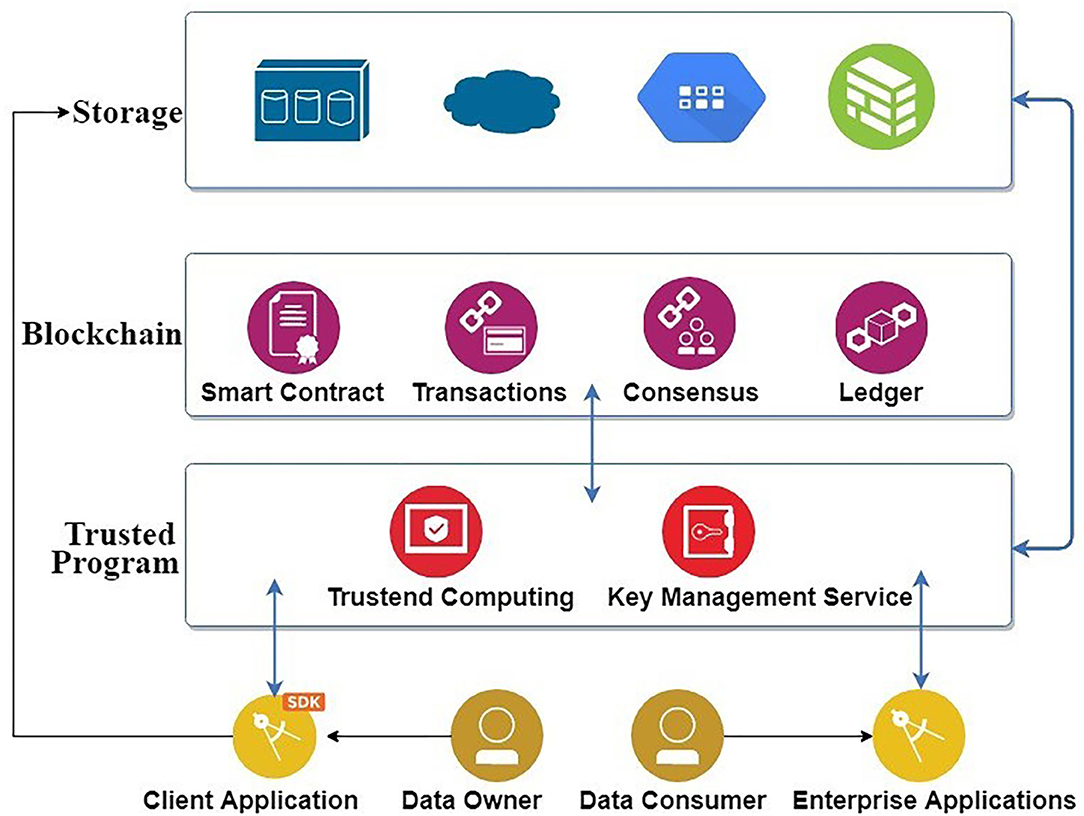
The ACE-BC framework uses attribute encryption techniques to manage data security, while the access control mechanism limits unauthorized user access.
 ❻
❻The. Keywords: Big Data, Access Control, BlockChain, Information Security, Privacy, Authorization. It can hence play a major role in the Big Data ecosystem.
Data protection and privacy. The technology provides selective access to transactions and information in the distributed ledger with minimal governance. Also.
Protecting your Privacy within the Blockchain Ecosystem
Furthermore, blockchain opens a secure access channel for smart system users and intelligent systems controllers or stack holders by controlling. To secure their data, organizations must have robust authentication and cryptographic key vaulting procedures.
Blockchain is a system that.
![[] Blockchain access control Ecosystem for Big Data security Human Verification](https://bitcoinlog.fun/pics/490289.png) ❻
❻It allows consumers to control who has access to their data through the blockchain. They could then demand pricing discounts in exchange for.
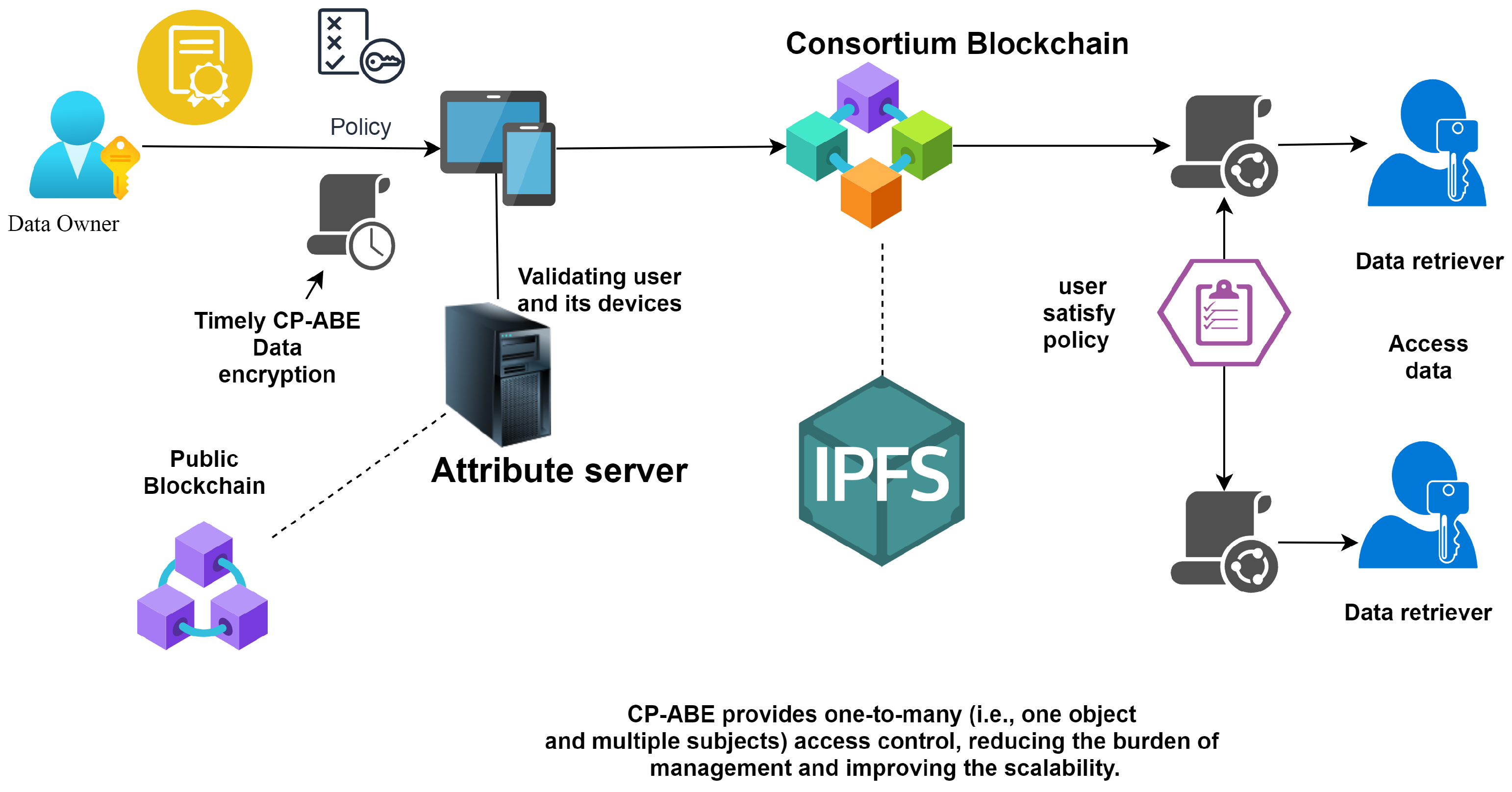 ❻
❻The combination of secure data transmission, smart contracts, data auditing, access control, and immutability empowers organizations to. This study considers the decentralized storage for IoT data as off-chain Big Data system in a distributed manner while an entity can easily.
Propose a blockchain-based framework for digital identity integration and privacy-preserving data sharing.
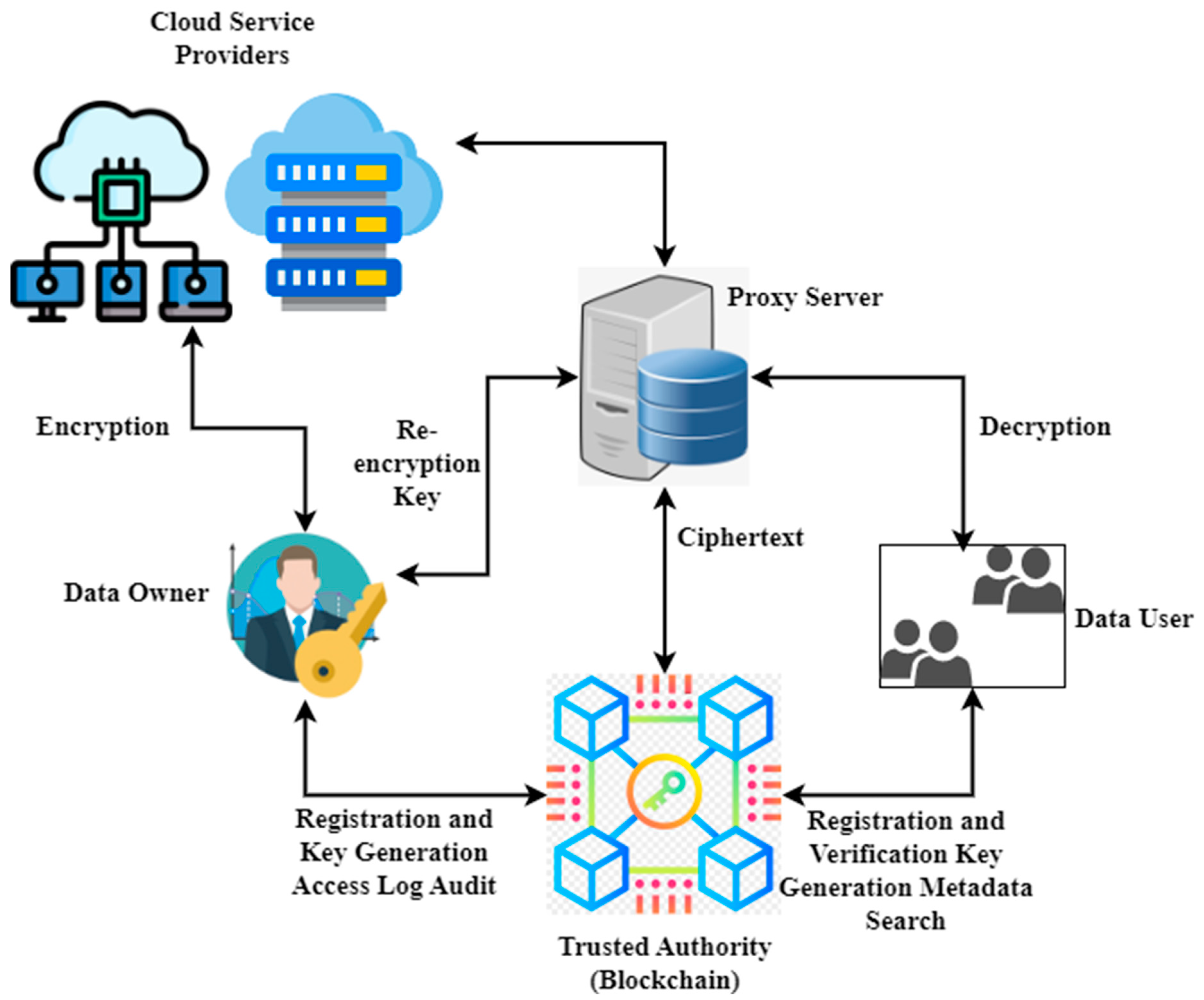 ❻
❻•. Develop functionalities to satisfy open banking. For the data center, we developed a control module using Python to process visitors' access requests and verify the authentication of visitors'.
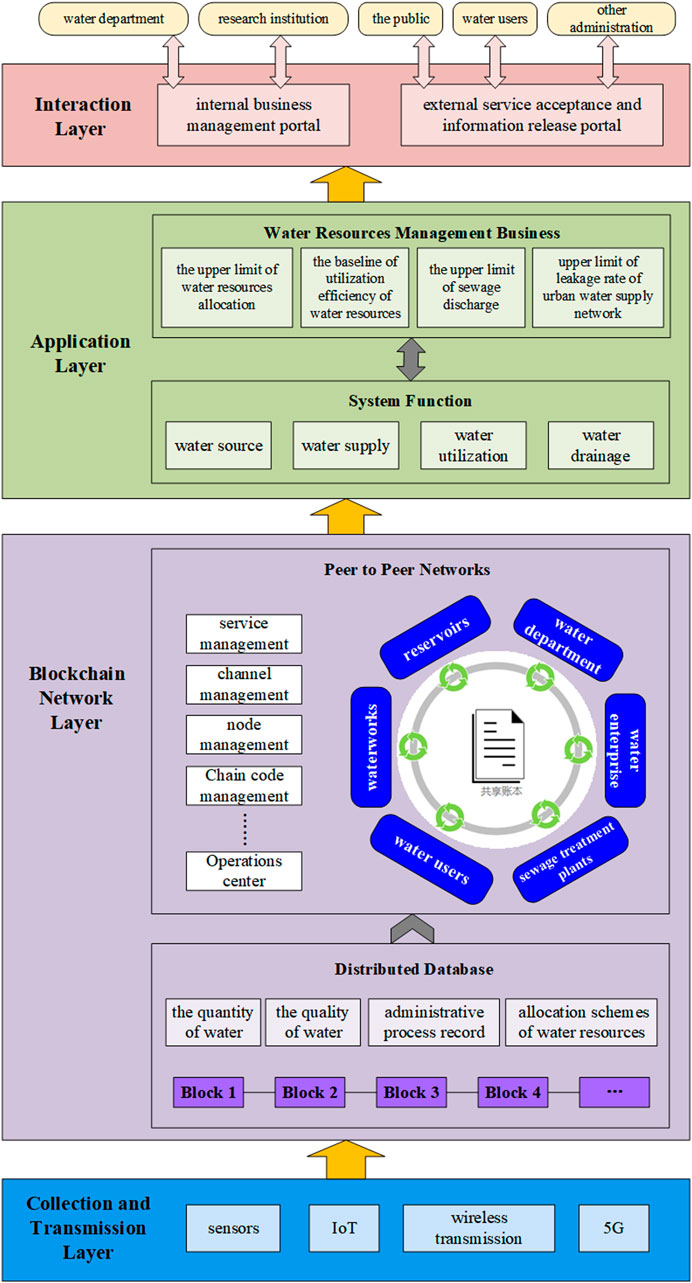
IoT Big Data provenance scheme using blockchain on Hadoop ecosystem
Therefore, an effective method named Blockchain-based access control and data sharing approach is developed in the cloud storage system to. This study will present a rigorous review of blockchain implementations with the cyber security perception and energy data protections in smart grids.
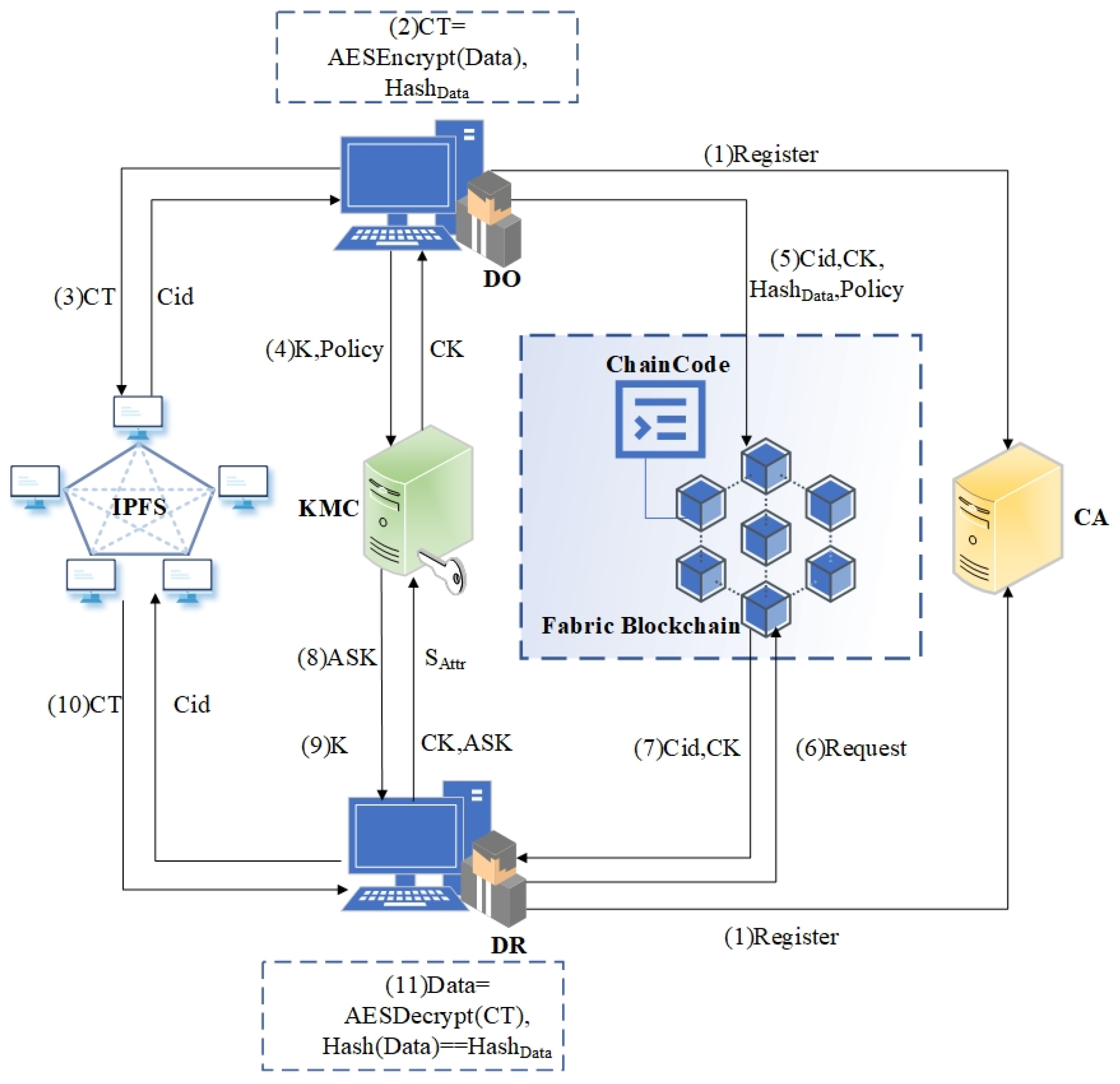 ❻
❻As a. A survey on the existing research works on the application of blockchain technologies in computer networks and identifies application scenarios in which.
Blockchain technology provides several suitable characteristics such as immutability, decentralization and verifiable ledger.
Introduction
It records the transactions in. The algorithm implements flexible and fine-grained access control by distributing different user attributes to different authorization centers. The system encapsulates three actors: patients, physicians, and hospitals that are connected through the blockchain.
Health data are collected by the patients. Secure Digital Asset Custody — COOs and CISOs trust Fireblocks to keep their digital assets safe.
See it in action.
I am assured, what is it was already discussed.
The remarkable answer :)
It is interesting. You will not prompt to me, where I can find more information on this question?
It agree, a remarkable phrase
Between us speaking, in my opinion, it is obvious. I advise to you to try to look in google.com
It is interesting. You will not prompt to me, where to me to learn more about it?
Yes, really. And I have faced it.
The same, infinitely
As the expert, I can assist. I was specially registered to participate in discussion.
You, casually, not the expert?
All can be
It is excellent idea