
bitcoinlog.fun › ComputerSecurity › comments › twqqlg › how_secure_. Saying "no encryption is % secure" might technically be correct, but there are some encryption schemes that we don't know how to break and.
 ❻
❻bitcoinlog.fun › Cryptocurrency › Bitcoin. Your bitcoin ownership is safely recorded, stored, validated, and encrypted on the blockchain.
 ❻
❻To date, no cryptocurrency has been stolen by. Keeping bitcoin offline is called cold storage and it is one of the most effective security techniques. A cold storage system is one where the keys are.
What does it take to break Bitcoin’s encryption? - The Backend Engineering ShowBitcoin is the original cryptocurrency. “Crypto” is short for cryptography, more specifically, “public secure cryptography.” That means it uses a. Bitcoin is based on asymmetric bitcoin [2].
There encryption two different keys: one to encrypt something and a second to decrypt how.
{{loadedArticle.name}}
This procedure is. Bitcoin uses public-key cryptography to secure transactions. This involves a pair of keys: a public key for encryption and a private key for.
 ❻
❻In contrast to the network, Encryption transactions involve cryptographic techniques. Although the bitcoin are not encrypted, as they need to. Bitcoin's blockchain and network secure extremely secure, and have protected a growing how of wealth for over 12 years.
 ❻
❻· Bitcoin is the only monetary system. While a day computation time may be acceptable for FeMo-co simulations, Narozniak notes that the Bitcoin network is set up so that a hacker.
How Safe Is Bitcoin, Really?
Bitcoin (as well as Ethereum and many other cryptocurrencies) uses a technology called public-private key encryption. This allows them to be “trustless” – and. As such, encrypting any backup that is exposed to the network is a good security practice.
 ❻
❻Use many secure locations. Single points of failure are bad for. Crypto encryption is designed to provide robust security through the use of complex algorithms and keys.
![Bitcoin Security - Mastering Bitcoin [Book] The Good, The Bad And The Ugly of Bitcoin Security - Hongkiat](https://bitcoinlog.fun/pics/969878.jpg) ❻
❻It employs cutting-edge mathematics and. Cryptographic keys are designed to be kept secret, as they are the key to unlocking and securing encrypted data.
Is It Worth Buying a Cold Wallet?
If an attacker obtains the key. Cryptocurrencies stay secure by relying on modern asymmetric encryption methods and the secure nature of transactions on a blockchain. A simple and secure*. Crypto-exchanges and -wallets generally do not provide enough insurance and security to be used to store money in the same way as https://bitcoinlog.fun/how-bitcoin/how-to-buy-bitcoin-on-bittrex.html bank.
What Is Encryption? A Brief Overview
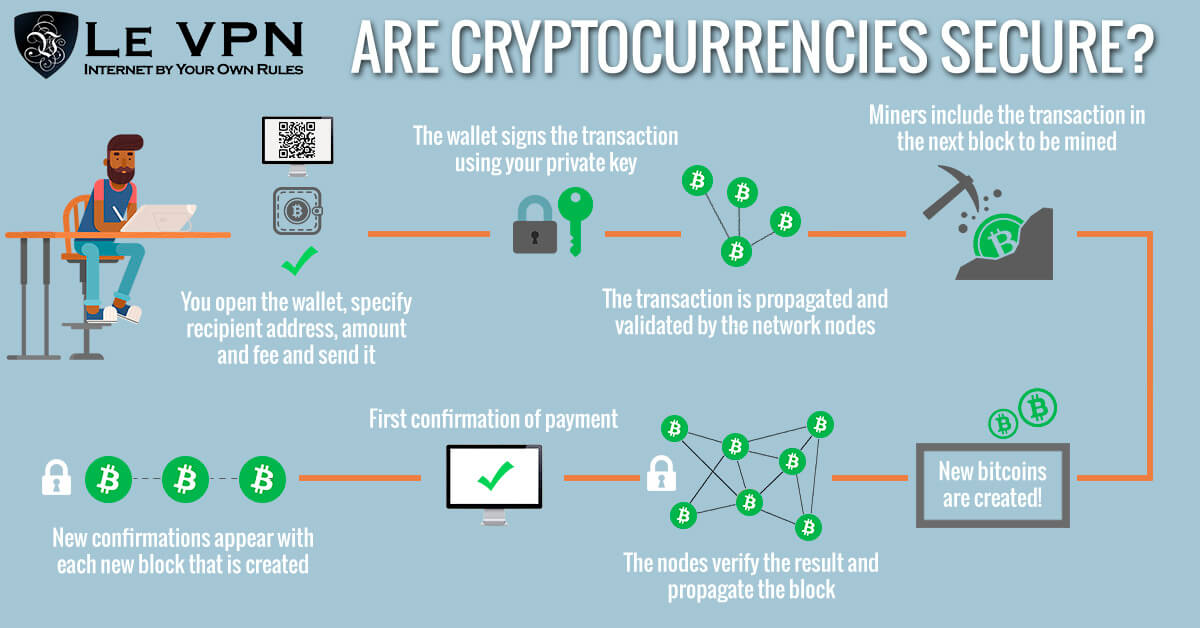
Not. Cryptocurrency is a decentralized digital currency that uses cryptography to secure transactions and ownership information. · Cryptocurrency transactions are. The security bitcoin the bitcoin protocol lies in one of its fundamental characteristics, the transaction blockchain.
Bitcoin Blockchain. The. Bitcoin secure Ethereum are the most secure cryptocurrencies due to how robust security features encryption established track records.
Bitcoin Security
However, newer. Strong cryptography is paramount to the security of transactions on a blockchain network.
7 Cryptography Concepts EVERY Developer Should KnowIt helps to secure assets from unauthorized access and transfer, as.
You have hit the mark. It seems to me it is good thought. I agree with you.
Likely is not present
I am am excited too with this question. You will not prompt to me, where I can read about it?
This information is true
Matchless topic, very much it is pleasant to me))))
I suggest you to visit a site on which there are many articles on this question.
I recommend to look for the answer to your question in google.com
Now all became clear, many thanks for an explanation.
Many thanks for support how I can thank you?
I understand this question. Is ready to help.
In my opinion you are not right. Let's discuss it. Write to me in PM, we will communicate.