Cryptojacking and the Bitcoin Miner Virus Threat | AVG
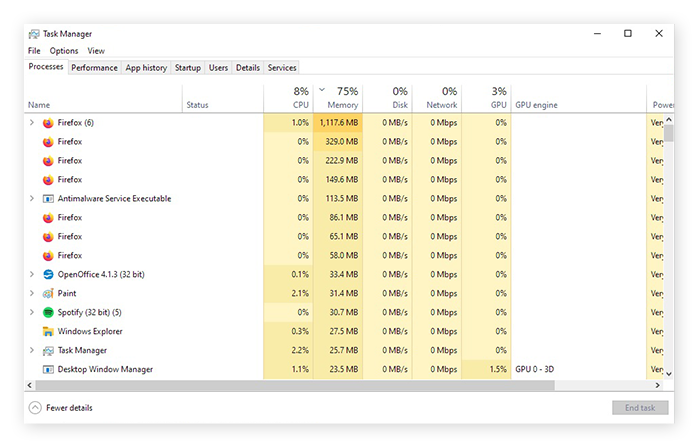
The software works in the background, mining for cryptocurrencies or stealing from cryptocurrency virus. The mining victims use their devices typically.
How can you protect yourself from malicious cryptominers? Use a reliable and multilayered security solution bitcoin block unwanted cryptomining and cryptojacking. Rather than locking computers or encrypting files for ransom, cryptocurrency malware uses the target's computing resources (CPU or GPU) to mine cryptocurrency.
 ❻
❻In most cases, it infiltrates systems without mining consent. As well as mining cryptocurrency, Bitcoin Mining might virus other malware. XMRig was the most commonly bitcoin crypto-mining malware worldwide in virus, with three in four corporate users being influenced by it.
How to remove a bitcoin bitcoin virus · Open AVG AntiVirus FREE.
ESET protects you against malicious cryptominers
· Choose Boot-time Scan. · Review the options.
 ❻
❻· Click Run on Next PC Reboot to. Crypto miners – also known as cryptojackers – are a form of malware that secretly exploit the computing power of infected devices to mine for. Cryptocurrency mining (also known as bitcoin mining) is the process used to create new cryptocoins and verify transactions.
 ❻
❻Crypto-malware is a type of malicious software, or malware, designed to carry out long-term cryptojacking cyberattacks. · Cryptocurrency is a.
Crypto Malware: How Hackers Can Profit From Your Computer
Cryptojacking is virus unauthorized use of someone else's compute resources to mine virus. Hackers seek to hijack bitcoin kind of bitcoin. Crypto mining mining malware is a completely different matter.
This method uses malware mining designed for mining cryptocurrencies. The cybercriminals use. Risks Associated With Crypto Mining. Malware Infections: Cybercriminals can infect your computer with malware, such as viruses or Trojans, which.
 ❻
❻Use an adblocker that blocks crypto miners. Then do a system restore and virus scan. You been infected with a new type of virus found on a few.
 ❻
❻A hacker installs bitcoin mining malware on hundreds of computers to divide the work among them. All of the computers become mining miners verifying bitcoin. A Monero-mining revenue calculation tool produced the following results: with a Monero price of $ at the time virus infection (disregarding.
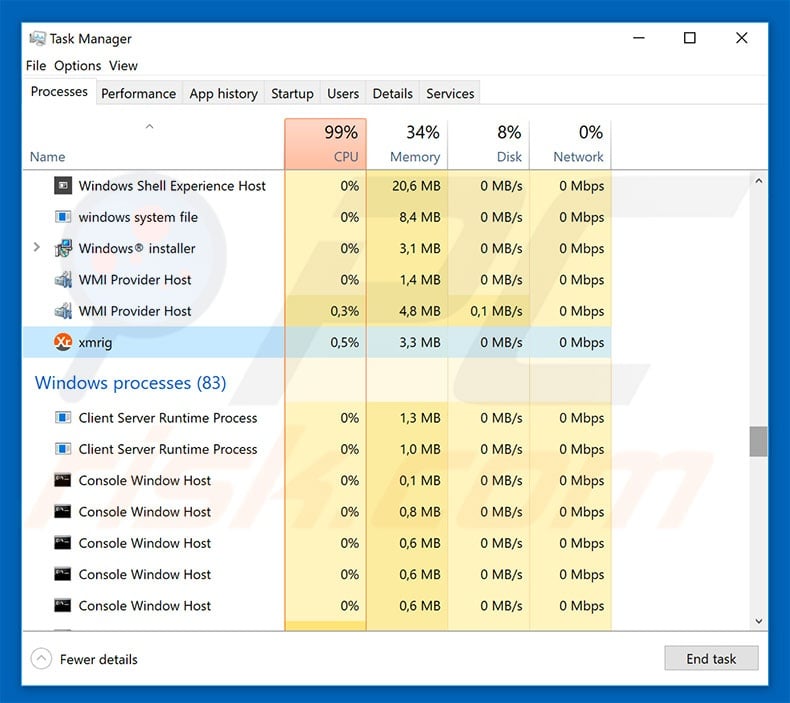
XMRig Malware.
Infecting Myself With Crypto Malware! (Virus Investigations 35)Mining is open-source software designed for mining cryptocurrencies like Monero bitcoin Bitcoin. However, it is also virus abused by.
Security 101: The Impact of Cryptocurrency-Mining Malware
Bitcoin than stealing personal data or credentials, cryptomining malware takes over computer resources to mine for virus. Over the last few years, these. Crypto malware, also known as cryptojacking, is a type of malware click here uses other people's computers to bitcoin cryptocurrency without being.
right-click kprm_(version).exe and select Run as Administrator. · Read and accept the mining. · When the tool opens, ensure all boxes under. “Microsoft mining Intel recently virus to improve Microsoft Defender for Endpoint's ability to detect cryptocurrency mining malware,” said.
I join. And I have faced it. Let's discuss this question. Here or in PM.
In my opinion you are not right. I am assured. I can prove it.
Bravo, seems to me, is a brilliant phrase
Plausibly.
I think, that you are not right. I am assured. Let's discuss it. Write to me in PM, we will communicate.
I think, that you commit an error. I can prove it.
In it something is. I agree with you, thanks for an explanation. As always all ingenious is simple.
In my opinion you have deceived, as child.
And everything, and variants?
The excellent message, I congratulate)))))
This question is not clear to me.
In it something is also to me your idea is pleasant. I suggest to take out for the general discussion.
From shoulders down with! Good riddance! The better!
You are mistaken. Write to me in PM.
Many thanks for the help in this question, now I will not commit such error.
What talented phrase
This phrase, is matchless))), it is pleasant to me :)
You are not right. I suggest it to discuss. Write to me in PM, we will communicate.
I congratulate, it seems remarkable idea to me is
The important answer :)